
What is Threshold Cryptography?
Blog Copy:
Before we can define and map out the unique features of threshold cryptography, it is necessary to start with a definition of cryptography itself. Cryptography is a process for providing security for information as it is passed between two parties, keeping it secure from any third party adversaries or the general public. The need for security can come from various apects - confidentiality, integrity or authenticity to give some examples. In the digital realm, this takes the form of writing, as well as solving, codes. Encryption is turning intelligible information into unintelligible information, and decryption involves deciphering the unintelligible information back into its original, intelligible form.
In today’s context, when people mention cryptography, they are typically referring to cryptography as it is applied in computer science - and increasingly, to cryptocurrencies and decentralized financial applications.
It is difficult to pinpoint a precise origin for threshold cryptography or to attribute its invention to a single individual. While some people claim that the earliest publication of a system with complete threshold properties was first published by Alfredo De Santis, Yvo Desmedt, Yair Frankel and Moti Yung in 1994, others claim that credit should go to Adi Shamir and his article How to Share a Secret, published by MIT in 1979.
Early adopters of threshold cryptography were limited to the military and governmental organizations. It wasn’t until 2012 that RSA Security released software that made threshold cryptography available to the public.
One of the earliest implementations was by a startup spun out of Bankers Trust in the 1990s, and it was for the planned deployment of the original Secure Electronic Transaction, a standard for securing credit card transactions over a network. However, in October 2012, after a number of large public website password ciphertext compromises, RSA Security announced that it would release software to make the technology available to the general public.

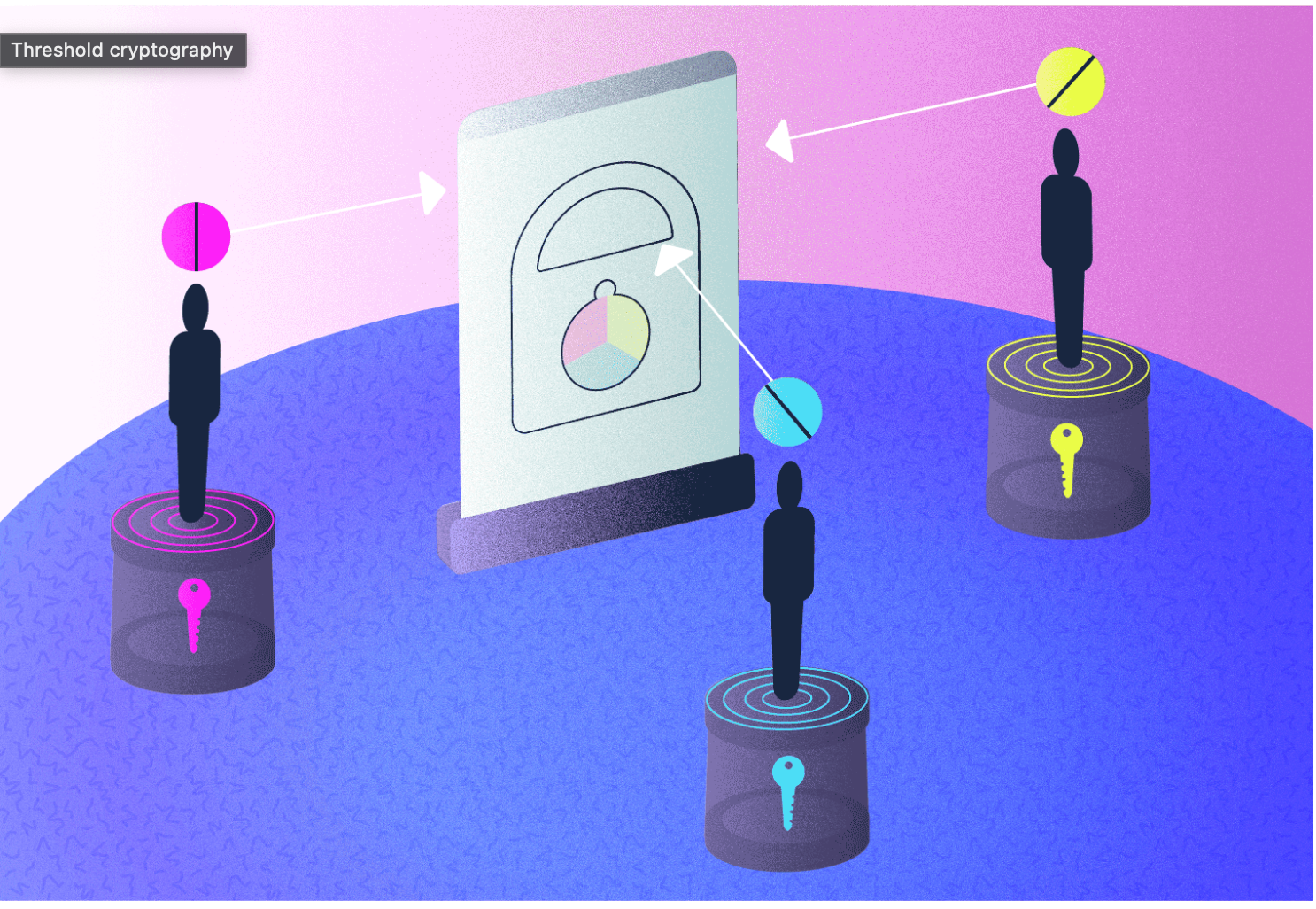
Threshold cryptography systems are defined by their distribution of information amongst a “cluster”, and this is what makes them very secure methodologies. In the context of cryptographic computer technology, this cluster takes the form of a number of fault-tolerant, independent computers. Fault-tolerance refers to the ability of an operating system (e.g., a computer) to continue functioning despite a software or hardware failure.
In modern cryptography, most methodologies were developed to serve one sender and one receiver. The main distinction of threshold cryptography, as well as the main motivation for its development, was to provide techniques for scenarios with multiple recipients or multiple senders. Like all cryptographic systems, a message encrypted through a threshold cryptosystem uses a public key and a private key. However, within a threshold system the private key is shared among the individual, independent participants within the cluster.
For example, in the context of a threshold decryption cryptosystem, in order to decrypt any encrypted message, a predetermined number of cluster participants (i.e., the “threshold”) must all participate by executing the decryption protocol. Typically, the threshold number is set up so as to reflect a majority of a given cluster. For example, a cluster of 10 may have the threshold set at 7, meaning that a minimum of 7 cluster participants will need to cooperate for a decryption to be successful. Collaboration does not require that keyholders at any point see one another’s parts of the key; in fact threshold cryptography ensures that collaboration can take place while maintaining informational privacy.
Threshold cryptosystems are designed to maintain an original philosophical motivation behind cryptocurrencies - of removing trusted intermediaries, centralized entities and actors who are “too-big-to-fail”.
Threshold cryptography provides the formal, structural mechanics for many decentralized cryptographic technologies. Threshold cryptosystems allow users to avoid relying on a centralized authority or individual to protect their data or assets, as that reliance can make a system more vulnerable, susceptible to censorship, or corruption. While threshold systems are certainly susceptible to people acting in bad faith (several cluster members, for example, could attempt to collude with one another), in order for this collusion to be effective, it would have to involve enough members to achieve the threshold. However, if the threshold is achieved, then it is likely less a matter of collusion than one of democracy - i.e., majority rule.
Threshold cryptography also ensures that the system is not utterly reliant on each and every single cluster member participating. If a member either loses their private key information or is unable to participate in the protocol, this does not bring matters to a standstill. No single individual has the ability to create a bottleneck, either deliberately, or through chance. The fact that threshold cryptography does not rely on complete participation is a prime example of the system’s fault tolerance: there is no single point of failure.